Transcript
Opening
Welcome everybody to What's the Problem, the show that explores problems that buyers, practitioners, and professionals in the cybersecurity space face in today's world. Today, we are lucky to have Fatma Candas with us from halfway across the world.
Conversation
Mike Krass: Fatma, say hello to everybody that’s listening.
Fatma Candas: Hello everybody. It’s great to be here.
Mike Krass: We're excited to have you. Let’s get right into it! Fatma, tell our listeners why you're qualified to talk about security.
Fatma Candas: I've been in the IT industry and moved towards cybersecurity in the private sector. I started my career at an IT company that sells IT hardware products and software solutions to private and public sector companies and individuals. My position was IT specialist, basically selling our products and services and providing technical support to our clients.
It was a technical sales engineer role, and there's a lot of client engagement around security. It was a fabulous experience. I deep dive into cybersecurity by being certified Concierge Security Plus and other education. Currently, I'm working in a fantastic cyber security training and consulting company as a cyber security consultant to conduct various security assessment projects and provide consultancy to our clients regularly.
Mike Krass: That is a long list of qualifications. We are excited to dive into the second question in our show, knowing that you have that background, so Fatma, name a problem in the security world.
Fatma Candas: The main problem is vendors focus on themselves instead of buyers. The buyers' specific problems indirectly decrease the effectiveness of the company's security posture. Vendors are technical sales engineers and consultants reps, and there are many names, but I will call them vendor for simplicity. So vendors just focus on their products and services like “This is me, and this is my service and product. It's all about me.” It is not solving the buyer's security problems point to point. It is less effective than we think from a security perspective. So instead of focusing on themselves, they should focus on the buyers' needs and pain points and ask intelligent questions such as “What is your specific problem? What are you dealing with right now? What keeps you up in the middle of the night? Let's see how I can help.” After listening to them and learning about their specific problem, they should properly offer a customized solution to their specific problem. Maybe they just need an endpoint detection and response solution, not an endpoint protection platform. They need a recovery solution in addition to a backup solution. Focusing on the buyer-specific pain points or problems mindset will have a tremendous effect on the buyer's security posture, which means the company's security posture and increases the vendor's effectiveness and success rate. There are a few things to pay attention to. First, vendors need to showcase their customized solutions' value and impact on building recognition and trust between the two parties. And let's say the vendor explains to the buyer this properly configured firewall router will eliminate 84% of common breaches. When the buyer is at that first, it builds recognition and trust in the vendor, and also buyer believes that the vendor can solve their specific problem and help them.
Vendors shouldn't bore people with the technical details if they aren't talking with the technical person in the company. Finding the right peer is important within the conversation and presentation. Another main point is vendors should have a conversation instead of giving a presentation. There's a good example there. Once as a vendor, I was in the buyer's office and asked them their specific problem pain points, and they opened up themselves and end of the conversation. They were impressed and shocked. They said, ‘’No one comes to us and asks us our specific problems and listens,’’ and they said ‘’they just come in and plug in their computer, read off their slides, and that's it’’ So obviously, buyers focused mindset will have a tremendous effect.
Mike Krass: If I could jump in and repeat back to you because you use two words directly and indirectly. You talked about it being a conversation as opposed to a PowerPoint presentation or more of a one-way, one side of the discussion. The other thing you didn't say, but I heard it's a consultative discussion. I think you mentioned EDR. Do we need endpoint detection and response? Do we need the protection of our endpoints, or are we just okay with detecting and then responding? I hear from you that it's a consultative exercise, conversation, and understanding of what they are going through. Even though they have products that can be sold one to many, you have to understand how to apply those products to a customer. A vendor needs to understand how to apply those to a customer's problems. Otherwise, it doesn't sound like it's a very pleasant experience to sit through those vendor meetings. Is that what I hear from you?
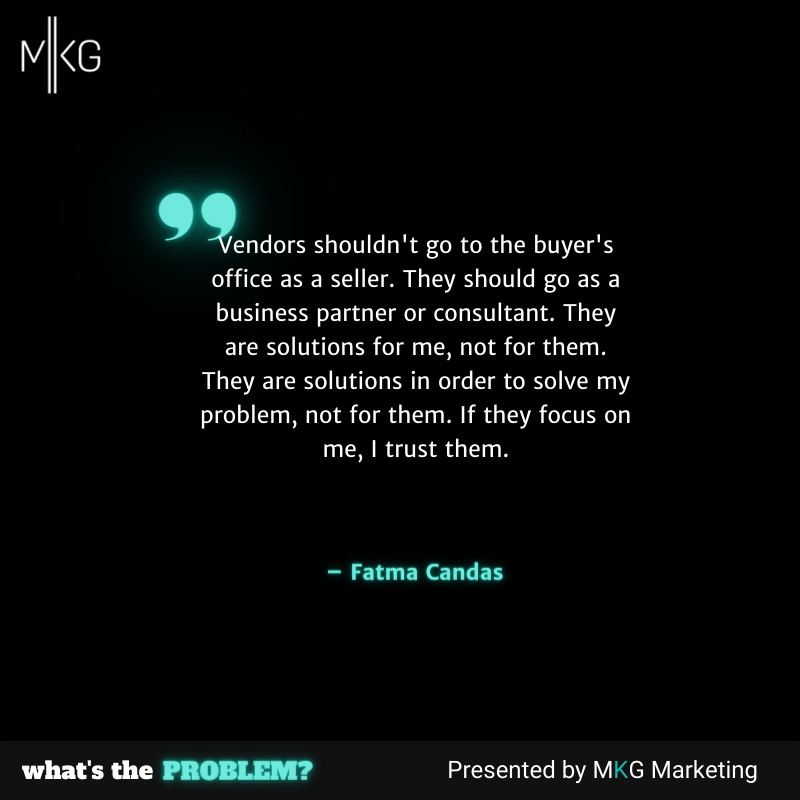
Fatma Candas: Absolutely. The vendors shouldn't go to the buyer's office as a seller. They should go there as a business partner or consultant.
Mike Krass: Question for you. How do you know these vendors are coming through your office? How do you know to trust them? What if they're good conversationalists? How do you know you can trust that their products will solve your problems? How do you go about that?
Fatma Candas: If they focus on me and my problems, I can trust them. If they focus on their products, I might think to trust them.
Mike Krass: Got it. You put an incredible emphasis on “If you're focused on me and my problems” That's huge that builds a bridge of trust right there for you. And as long as you keep it focused on me and on my problems and how, you have these solutions, but again, they're focused on problems. We'll talk about the solutions eventually, but let's focus on you that build that bridge quickly.
Fatma Candas: Exactly. Because they are solutions for me, not for them. They are solutions in order to solve my problem, not for them. If they focus on me, I trust them.
Mike Krass: I like it. You are very clear. Anyone, anybody, or whoever wants to walk into your office now knows how to treat the conversation. So we're doing everybody a favor in the future. As we wrap up this question, is there anything else around focusing on the buyer's problems that you want to highlight?
Fatma Candas: I would like to highlight having a conversation instead of giving a presentation. Being empathetic based on the buyer's pain points and presenting relevant information is crucial. There is a huge difference between the regular technical sales presentation and customer-focused conversation. The security world is constantly changing, and there is no fix and forget. It's just an unending process for both sides. There is no doubt that buyers should constantly check and validate their defenses. On the other side, vendors should improve themselves according to buyers' specific needs wisely. So with this mindset, we'll make the world more secure.
Mike Krass: One more follow-up before we get to the fun question.
Fatma Candas: Sure.
Mike Krass: Empathetic and relevant information. Say you first meet a vendor, how do you want them to give you information? Is it technical datasheets, videos, or webinar recording? What do you want to receive from them the first time you meet them?
Fatma Candas: It depends who they are talking to. If they are talking with the technical person in the company, I would like to hear their technical details and relevant technical details according to my problem. If they are talking with the less technical people like a manager type of roles within the position and the company, one or two key technical points and then the impact and value of their solution to solve my problem.
Mike Krass: Got it. Speaking to a technical again, first meeting the technical individual, it's like, let's open the hood.
Fatma Candas: Asking their specific problems, listening to them, and while listening, the vendor probably builds up some of the solutions for the buyer. If they are not, they can make another meeting to give their specific solution to the buyers.
Mike Krass: Got it. Fatima, I really appreciate it. I know that the listeners also appreciate sharing your thoughts and experience. It's been a real pleasure here, and as promised, it is time for the fun—the third and final question of the podcast episode. Fatma, tell us about a terrible haircut you've had one time.
Fatma Candas: Mike, how fast we came back because when I was in high school and a teenager, I went to the hairdresser and said, ‘’I'm bored. Let's try something new’’. And she made a haircut for me, and when I looked in the mirror, it was very weird in front, it's diagonal and long. The back is a short straight cut, and it seems like two different people within one hat. That was my worst haircut, and I couldn't even tie my hair with the clips, so I just used hair clips to open up my face a little.
Mike Krass: Yes, exactly.
Fatma Candas: I had a long time time to fix it.
Mike Krass: Well, I like that it is summarized nicely. It was basically like two people's heads all on the same head. I can only imagine how unhappy you were to have that hairstyle in terms of the haircut.
Fatma Candas: She probably tried the first time on my head.
Mike Krass: Maybe two different haircuts.
Fatma Candas: She couldn't miss the opportunity.
Mike Krass: Yeah. I got my lesson, though.
Fatma Candas: I didn't say, ‘’I'm bored. Let's try something new’’ to any hairdresser after that. At least you learn something that those are words you don't tell hairdressers yet.
Mike Krass: We appreciate you spending some time with us today. And to the listeners, thank you for listening to What's the Problem, the show that explores problems that practitioners, professionals, and business folks in the cybersecurity space in today's world until the next episode. Say goodbye to everybody.
Fatma Candas: Goodbye, everybody. Take a good day.
Fatma Candas
Fatma Candas is a cyber security specialist at the Peak Cyber Institute. Her “why” is to secure an efficient digital world for everyone. Prior to Peak Cyber Institute, Fatma worked in IT at Nilcom Computer Systems. She has a degree in mathematics from Dokuz Eylul University in Turkey.



