Transcript
Opening
Hello, everybody, and welcome to What's the problem, the show that explores problems in the world of cyber security.
Today, we are fortunate to have Ambuj Kumar joining us on the show.
Conversation
Mike Krass: Ambuj, say hello to the listeners.
Ambuj Kumar: Hi, Mike. Excited to be here.
Mike Krass: Excited to have you, and I'm excited for you to answer the first question here. So can you tell our listeners why you are qualified to speak about security?
Ambuj Kumar: I'm the co-founder and CEO of Fortanix. We are data first multi-cloud security company. And for the last six years, I've been thinking about security for most of my waking seconds, but I have a deep background in computer architecture. I hope to have some meaningful things to add here.
Mike Krass: Absolutely. And just to help you brag about yourself and your experience, you also told me that you had invented a few things in the security world.
Ambuj Kumar: Yeah, so there's a new type of security. We'll chat a little about confidential computing, which focuses on keeping data secure in use. Fortanix is the pioneering company behind that. It was our Genesis, and we were the first company to productize it. Now we see a big market momentum towards keeping data secure. It’s not bragging, but we were the first one to see the need for securing data throughout its lifecycle and the first one to implement it.
Mike Krass: I love it. And you jumped into the beginning of our second question when we spoke. Earlier, we were talking about the three states having data. It's at rest, in motion, in use, and getting into confidential computing. Talk to our listeners about problems protecting data in use.
Ambuj Kumar: That is interesting. If you think about how much sensitive information you have on your phone, it has all your pictures, financial information, and many other things. But if somebody takes your phone away, they will not get your pictures out. Your pictures are encrypted with keys, and those keys are derived from the PIN code you enter when you start your phone. Encryption security, or data address, then you think about data in motion.
Let's say you log into your favorite bank's website. So data that flows from your laptops and browser to the bank server goes encrypted using a technology called TLS. And if you think about how powerful that encryption is in keeping data in motion, it's amazing. Imagine just how many different stages your data goes through. There is a router in your home; your data goes there, then it may go to the Verizon tower with access. It gets processed there. It flows through various network pipes. Lots of people look at it, and maybe sometimes it goes through an undersea cable. And finally, it reaches your bank's server.
We never worry about our data being accessed in that transit because it's encrypted. When it leaves your browser, it goes encrypted until it reaches your bank's machine. And that is the power of encryption and keeping data security in motion. But then think about what happens once the data reaches the bank's server and gets processed. The first thing that happens is that data gets decrypted, and at that point, it becomes a sitting duck for anybody inside the network. Anyone who can start any malware or any bad software or can steal your data and use traditionally have not been secured using encryption. So that's what we focus on doing, keeping data secure at rest in motion.
Mike Krass: Talking about protecting data in use, I know you have an engineering background, so let's get into some technical components a little bit here. What are you doing that's different from what anyone else has been doing?
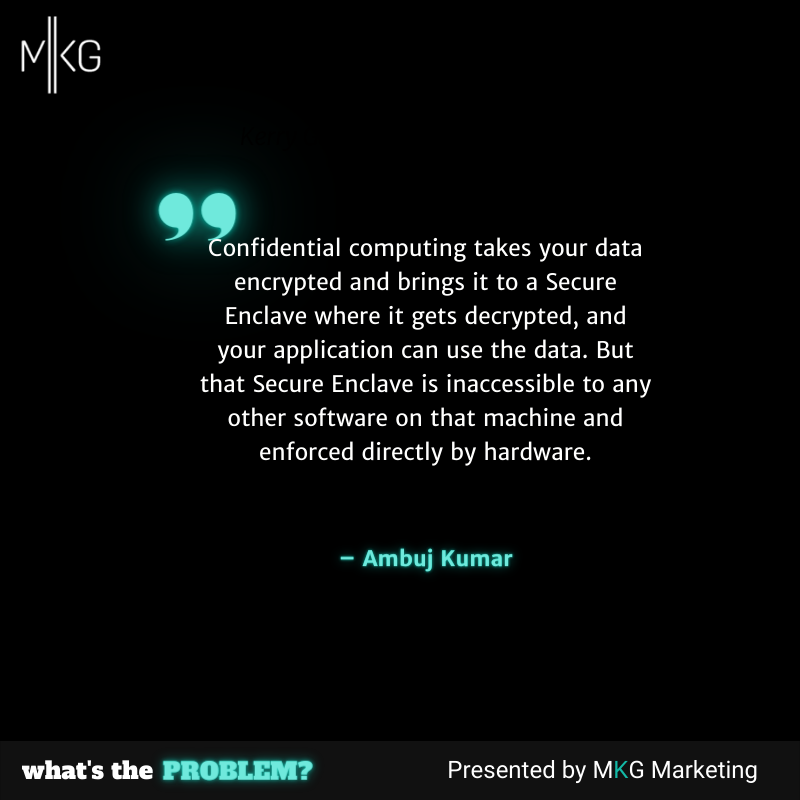
Ambuj Kumar: We use confidential computing technology that allows you to process your data in an untrusted environment. Computers work because there is a root user, an operating system, privileged software, a bunch of drivers, etc. And if any of those thousands of components are bad, the whole thing collapses, and that is because of how memory is protected. Confidential computing takes your data encrypted and brings it to a Secure Enclave where it gets decrypted, and your application can use the data. But that Secure Enclave is inaccessible to any other software on that machine and enforced directly by hardware. I do not have to trust my operating system, my root user, and my IT admin, so the result is that, let's say, I have sensitive data that I'm processing in China, and I don't trust anybody in China. And even when they have physical access to the machine where my data is being processed, they can put any malware or virus and not get my data out. This is such an extreme level of security that it opens up so many use cases are lost, so much value of data that is just beyond amazing.
Mike Krass: I am not an engineer, although I understand what you're saying. I'm trying to help my fellow non-engineering listeners here in this enclave. Could it be compared? Not exactly, of course. But could it be compared to spinning up like a partition virtual machine or a cluster? If you're talking about containers, how is this enclave different from any of the things I just mentioned?
Ambuj Kumar: Good question, Mike. It is a partition on your computer, and the fundamental difference is that this partition is created and maintained by hardware, so your CPU. All of the partitions, your virtual machines, or containers, are created by software that runs on your machine. And if I'm a bad guy, I just muck with your software, confuse it, control it so that I get inside your partition, and then I can steal your data. But the way harvests are constructed, they are much more secure. Not that programmable.
Guess what if your hardware can create a partition and keep it secure? I cannot get into the partition even if your software is bad. It is somewhat similar to other technologies like containers or VMs because it's a group of memory accessible to some applications, but it is enforced by hardware. And that brings a new level of security.
Mike Krass: The other I thought that came to mind or synonymous example that came to mind is the concept of software sandbox, which you've very clearly said is secured by the physical hardware. And obviously, a software sandbox is something you're usually playing around in many banks such as JPMorgan Chase or HSBC that send a wire transaction from New York City through the underwater cables to London. And then they stuff it into a sandbox to see if they should process the wire transfer or not like that. That's not why you would use a sandbox, but in the same way, I think the word Enclave is almost like a production maintained by your physical hardware. It's a production sandbox, in a way, again, just using a synonymous phrase there.
Ambuj Kumar: Absolutely. Sandbox is the idea behind any kind of sandboxes. You keep bad things out. So now it is all question of how effective your sandbox is. If your Sandbox is maintained by software, then you are at the mercy of the software. The CPU maintains a sandbox, so you're still at the mercy of the CPU. But guess what? Your CPU does not get updated 100 times a day, and it's not running software written by 3 million people. It's not running a very programmable stack of a bunch of code. It's a much more content problem. And only somebody can go and reverse engineer how billions of transistors are laid out on the CPU. They would have a hard time defeating that sandbox, so think of the enclave as a hardware-enforced sandbox.
You do not have to provision anything at the hardware level. You can use it in the cloud and can verify it remotely. So let's say I give you my data. We understand that you will process my data only in this hardware enclave, and you want to process it outside because you want to use it for something I didn't authorize you to do. I can remotely verify that my data is going out of the Enclave, and I can do certain things that will make it impossible for you to process my data outside the hardware enclave. I can put some conditions so you can use my data only for the right application we agreed to. So even if in a way, you have access to my data, you cannot use it for any unauthorized use, which means that I can share my data. I can run AI on your sensitive healthcare data. Maybe I can try to find a cure for cancer without ever being able to compromise your privacy.
Mike Krass: Privacy is a hot topic right now. But probably the topic for another episode. That's a whole episode in and of itself.
Well, thank you so much for stepping us through Fortanix is up to educating the listeners on confidential computing and talking about protecting data in use. As we conclude this episode, we'll come to the last question: tell us about a terrible haircut you've had at some point in your life?
Ambuj Kumar: I might get in trouble for that. But my wife was my savior during COVID. One of the weekends, she was not very keen on cutting my hair, but I was, and that didn't end too well for me. I'll just leave it back.
Mike Krass: We share that experience during COVID. I also asked for and received a haircut from my wife, and it went okay. That is a big breakthrough because men, like the two of us, with shorter hair, tend to get haircuts more often than women. She always used to ask me, “ You're going to get a haircut again?” And the one breakthrough we had in our marriage was she started cutting my hair. She's like, “There's so much hair here.” And I was like, “This is what I've been telling you. This is why I get a haircut every four weeks. It gets out of control.”
Ambuj Kumar: Indeed, Mike.
Mike Krass: Awesome. Thank you so much for educating the listeners. I think listeners might want to reach out to you or speak to somebody from Fortanix. What's the best way for them to reach out to your business and also to reach out to you? How would you prefer that they communicate with you?
Ambuj Kumar: I'm available on LinkedIn and Twitter on Ambuj Kumar Fortanix. You can find us on our website. We will also be at RSA the first week of June. If you're traveling here, I'd love to meet you in person too.
Mike Krass: Awesome. Well, thanks for being on the show. If you would give a digital wave to all the listeners as we close out here
Ambuj Kumar: Thank you.
Ambuj Kumar
Paraphrasing Margaret Mead, "Never doubt that a small group of thoughtful committed technologists can change the world. Indeed, it is the only thing that ever has". Ambuj Kumar’s passion is to assemble and work with such a group. He’s a sucker for passionate people wanting to make a dent in spite of any challenges. At the moment, Ambuj is the CEO of Fortanix, a data-first multicloud security company.


