Transcript
Opening
Hello everybody and welcome to What's the Problem, the podcast where we dive deep into the most pressing issues facing cyber and data security leaders today. In each episode we are joined by expert guests who share their insights and their experiences on the challenges that they currently face in the world of cyber or data security. Whether you're a seasoned veteran or a new leader in this field, this podcast provides valuable info and some strategies you can take immediately to your organization to take your organization to the next level. So join us as we explore the ever evolving landscape of cybersecurity and discover new ways to tackle these different problems. This is What's the Problem. I am your host Mike Krass. Today, let's get started.
Conversation
Mike Krass: We are joined by Logan Wolfe. Logan, say hello to our listeners.
Logan Wolfe: Hi, Mike. It's a pleasure to be here and hello to everybody who's listening.
Mike Krass: Now, Logan, tell our listeners why you're qualified to talk about security.
Logan Wolfe: Well, I've been in cybersecurity for about 15 years at this point. I kind of started hands on and now I’m in more of a leadership capacity. I’ve led global cybersecurity initiatives within companies like McKesson during its merger with Rexel, I think in 2018. San Francisco International Airport. I've led Lloyd’s global threat intel practice across eight countries and also critical Telco initiatives within Canada. For example, Rogers’ 5G rollout. I'm now the founder and CEO of North America's fastest growing cybersecurity startup, actually, which is called Orna. We automate cyber incident detection and response, including regulatory compliance, across all business functions. That is in contrast with the IT centric approach our competitors take.
Mike Krass: You're in for a treat today, listeners, because Logan just mentioned that he's working in the private sector, the public sector, across countries. Across eight different countries. Telecom, talking about ports with the San Francisco International Airport. So I think you're actually pretty well qualified, Logan, to talk about regulations and enforcement. So when we talk about cybersecurity regulations, can you talk to our listeners a little bit about how that works with regards to the enforcement part of that policy?
Logan Wolfe: Absolutely. It's similar to how any other regulations are formed in the private sector. That is to say, for instance, what happens if you misrepresent your P&L or taxes or other financial information to, I'm Canadian, so to Canada Revenue Agency in this case? So in this case, they're typically specific bodies. In Canada, we have, for example, privacy regulations like PIPEDA or PIPA, and so on. And each provincial regulator is responsible for enforcing their provincial privacy and cybersecurity statutes. The Competition Bureau, on the other hand, is an independent law enforcement agency. And they also investigate false and misleading statements concerning customers’ privacy, for example. But the thing is, and that's kind of the catch 22 here, is that they investigate these pretty sporadically. And really, it's kind of based on their review of your submission. In the United States, it's somewhat similar. For years, the government has pressed companies to voluntarily report intrusions and data breaches. We now have some regulations around that. And so does the US, obviously. But lately, they have concluded that such good faith efforts are not sufficient because a lot of organizations fail to report these incidents. Let's just say for varying reasons. Some of them, maybe they're simply not familiar with them. And that does happen usually with smaller companies. In some cases, that's outright fraud, needless to say.
Mike Krass: We talked about the US and Canada and you didn't mention any other countries. In our discussions before, we talked about how the US has a very specific policy stance. Do you have a preference on how the US does policy versus other countries? And it would probably be helpful to actually name another country so we can stop saying the word “other countries.”
Logan Wolfe: Absolutely. The countries that are seen as the most productive and proactive in that space will probably be the United Kingdom and the US again. But in the US there was…This is actually kind of a global fallacy in this regard. The responsibility to defend cyberspace and folks’ individual information and privacy was sort of 50/50 between individuals or even small businesses and local governments or larger organizations. But here’s what we're seeing lately in the US. There's a saying, “When the US sneezes, Europe catches a cold.”
This is to say that Europe typically follows the US’s example, which I'm sure we'll see here. And same for Canada, actually. So there's a shift towards shifting that responsibility from individuals and small businesses to larger organizations and to software providers, for example. Recently the Biden Harris administration has released the new National Cybersecurity strategy in the US. And some of the key things are they're shifting that responsibility from individuals to organizations. And they're introducing potentially direct liability on these businesses, to the extent of gross negligence for not discovering or addressing vulnerabilities within these companies’ products such as software applications, for instance. That’s the first major point there. The second major point is, they're gonna significantly incentivize long term investments and cybersecurity initiatives that private companies can take advantage of and collaborate with the government on introducing those controls. How's that different from what was being done before? But it is fairly different. Like the fundamental recognition in that strategy is that a voluntary approach to securing critical infrastructure networks is inadequate. And that's no longer feasible with sophisticated threat actors like Russia, China, Iran, North Korea. And they just want to make sure that these controls are being proactively addressed. And they’re recognizing that a big part of that is supply chain risks. They're unable to rely on the breaches or the mitigation controls that these companies apply. So they want to be much more stringent on that. And the strategy is a policy document, not an executive order right now. But we'll see what happens with that. First of all, it needs to clear Congress. So essentially, that needs bipartisan support. It's a Republican dominated Congress at this point. Considering the China scares, the balloons and hacking, and then the TikTok thing. My feeling is that it's going to get that bipartisan support because I think there's unanimous agreement in regards to the fact that cybersecurity is a top priority in terms of national security of the United States.
Mike Krass: Let me jump in with a question. So just not as a security founder, but as a cybersecurity professional. Do you think that this policy document that the Biden Harris administration has submitted to Congress, do you think there are some teeth here? Or do you think that this is more posturing? Like we, as the United States, are trying to show strength but we're not quite backing it up with as much muscle as we could? Do you have an opinion there?
Logan Wolfe: Well, I do. I'm fairly opinionated in general. I think it's fragmented. So in regards to enforcement of this, let's say it does become a law or an executive order. All of these enforcement agencies, they're spread pretty thin verifying these claims. It could be an audit or whatever the case may be. It's effort and time consuming. So in regards to shifting the responsibility from consumers onto organizations, I don't think we're going to see an immediate effect. But where we will see that effect is in just the general kind of foreign policy stance that shows that this is a priority. So that's nice. But also, they didn't go into specifics as to which exact initiatives in terms of like collaboration with the government. Whether that's rebates or subsidies or some kind of subject matter guidance. But that sounds a lot more tangible to me. You know, in Canada, for instance, one of the points of mild yet persistent frustration to me is that we don't have a lot of initiatives from the subsidy perspective or like the grants and things like that that specifically address cybersecurity. So if you're a cybersecurity startup in Canada, you're more or less on your own. That is in contrast with things like green energy and clean energy initiatives and things like that. There are specific grants for those. But in the US, I think the landscape is substantially different because cybersecurity is much more in the forefront. And that is largely thanks to the fact that the US simply just gets attacked a lot more by highly sophisticated actors. Like China, for instance, which is after IP usually, or like Russia, which at this point is after money. They just gotta make some money because sanctions are starting to take effect.
Mike Krass: You mentioned Russia, China, etc. What is Iran and what is North Korea looking for as nation states when they're committing a cyber attack on the US?
Logan Wolfe: Usually it's either money or IP or some combination of the above. And it really kind of depends on the times in question. For instance, during the pandemic, like when COVID had just sort of taken hold in North America. We have seen that Russia, despite the fact that they're typically financially motivated. They were after COVID-related IP, and that would be vaccine research and things like that which they eventually were able to successfully compromise and steal and develop their own thing. I think it's called Sputnik vaccine based on that, which is a whole other podcast material based on that. They had to mandate for people to take the vaccine because even the Russians themselves were super wary about injecting themselves with that thing. Iran tends to focus on critical infrastructure. And the problem with that is that's just everybody's target these days: supply chains and critical infrastructure because they're already so strained. If you look at this semiconductor chip shortage, pharmaceutical/ medical, any kind of supply chains, they're very strained. That means that their high availability and resiliency requirements are that much more important today, when compared to a few years ago. So if one of those goes out of business. There's a ransomware attack, for example, or they're otherwise forced to suspend operation through a denial of service or whatever the case may be, they're much more incentivized to pay significant amounts of money. And now we'll have many more companies than before protected with insurance, like data breach insurance, which covers at least some part of that. And unfortunately, I feel like that almost enables cybercrime and cyber attacks on critical infrastructure entities.
Mike Krass: Yeah, it seems to be. And this is just me, as an American citizen. It seems to be with insurance. The evolution of these fender bender, I hurt my neck-type claims. And not to say that people who get in car accidents have not hurt their neck. Many of them have. But there are many…they’re called Personal Injury Attorneys down here in the United States. There are many of those folks who take those cases and there are sometimes questions. You can tell how delicate I'm trying to be here, Logan. There's sometimes questions over how badly did you hurt your neck? Did you hurt your neck at all? Are you just looking to submit a claim? You want to go into mediation with the insurance company. And a lot of those attorneys on the personal injury side representing those who have been hurt or claim to have been hurt know that with most insurance companies it's widely known you can probably get 50 grand out of them. That's like the number that insurance has said anything more that you're asking for… Okay, we're gonna put a legal team together. We're actually going to dedicate resources to figuring out if this is bogus or accurate. 50 grand and below, it's actually cheaper just not to even have to go and depose everybody and potentially have a long, lengthy, and expensive court case/ trial case. And so they know the exact number. I feel, like with insurance, the same thing will probably develop. These actors will find the magic number of how much can I ask for without really pushing the insurance company too far to get a quick Yes? I'm not sure if you've seen that happen yet or not. But it just feels like a natural extension. It's effectively like this engineered insurance scam that's kind of going on here. It's just going from the highway to your computer.
Logan Wolfe: You've hit the nail on the head here. Because this is already a pretty popular thing, some malware even has built in features. The purpose of these features is to essentially analyze the company's infrastructure, size and so on, to determine what is going to be the realistic ransom amount that the company can pay. Real current somewhere is notorious. Whether those attacks are on critical infrastructure and healthcare organizations, the United States and other countries, it was notorious for that. They would spend months within the infrastructure of the target, trying to analyze that information and come up with surprisingly “reasonable demands.” But there's no such thing as a cheap ransomware attack or any cyber attack for that matter. The average size of a breach, and that's just the direct costs, are between five and six million. Last time I checked. And there are the shadow costs or indirect costs such as loss of reputation, lots of customers, auditory costs, potentially. Things like that. They can be orders of magnitudes higher. But yes, insurance companies do recognize that. And actually, what we see in the market this year is a lot of these insurance providers, they're tightening the screws on their due diligence processes or they're upping their premiums because some of them have realized that they don't necessarily have adequate risk assessment capabilities that allow you to determine if a company is prepared to respond to a cyber attack. So they issue a policy, they issue a premium, then a company gets compromised like two months later. And then they have to pay . They're getting pretty tired of that.
Mike Krass: Yeah. The whole model insurance is built on is we can't be paying out more than we're taking in. It's a pretty simple equation on the balance sheet. Let's talk about the last question here. So we've discussed policy enforcement across a number of countries during this podcast episode. You lead a cybersecurity business. Out of everything that we've talked about today, what's the one thing you plan to do in the next 12 months with all this information?
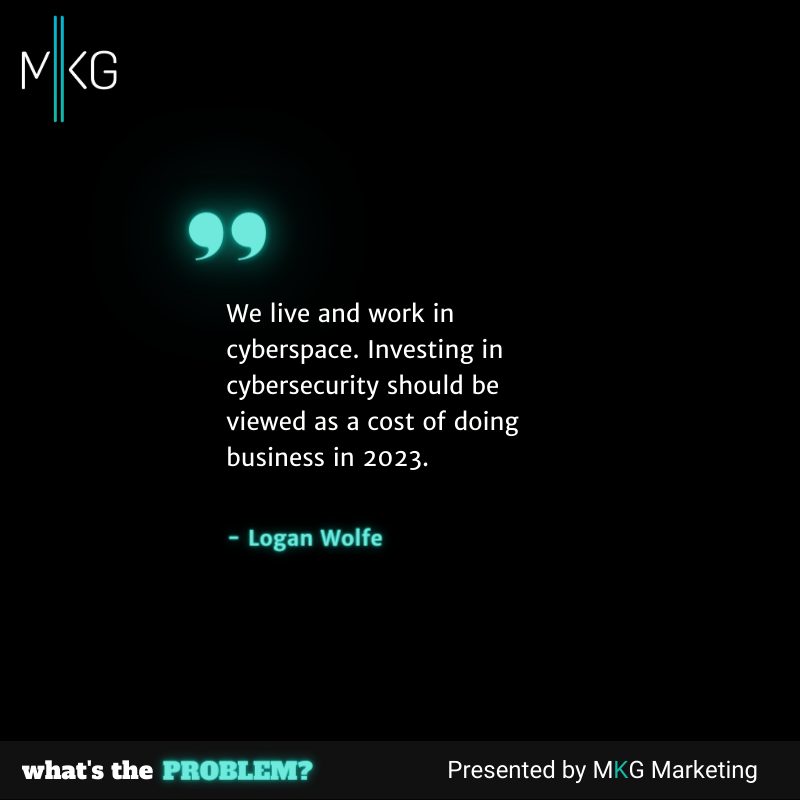
Logan Wolfe: Well, in a word, education. I've recently presented to the Canadian Public Sector, a cybersecurity kind of community hall. There are updates to a number of frameworks. Risk mitigation frameworks, that is. Such as NIST, for example, NIST 2.0. And NIST CSF 2.0 has been released. And really a big component of these updates is they're just trying to make the framework a lot more kind of applicable. They're introducing implementation guidance and things like that. Because a lot of companies, they just don't know where to start. Especially if you’re on the midsize or smaller side of things. There's also a shortage of cybersecurity resources in the job market, especially senior ones. So they don't know how to go about that. So us cybersecurity professionals are educating organizations on what are the top threats. What are the risks, what are the consequences of not addressing the cybersecurity risks? That’s key because there's still a bit of that perception, I think, even in 2023. Cybersecurity is a cost center. It's perhaps somewhat of an optional item. But that's not the case at all. You've probably heard this 100 times, but it's a cost of doing business in 2023. We are in cyberspace. All of these agencies, like the three letter agencies and the Five Eyes countries have recognized that years ago. You used to be able to get in a room with your adversary or your enemy and look them in the eye. But now they're just floating out there somewhere. So effectively, that's how the land landscape has shifted. In terms of risk mitigation, it's a priority for organizations. We just need to show them that. So the first one is education, like I said. And the second one is perhaps just the general cost benefit analysis to implement these controls. Again, it's the sign of the times. There's either a looming or an actual recession. It depends on who you listen to. It’s in the process of happening across the globe, but in North America as well. Cybersecurity budgets, especially stemming from that perception of cybersecurity as a cost center. They're not exactly growing. They're either shrinking or perhaps staying the same. So we see a lot of leaders looking to essentially extract maximum value of their cybersecurity vendors. They're consolidating solutions. They're consolidating vendors and may be in need of guidance on how to do that. So maybe a new cybersecurity strategy and perhaps incentives from the US government are going to help. But also us, as leaders in cybersecurity, we need to give people specific advice. I see a lot of general advice out there. That advice needs to get a lot more specific. People talking in podcasts and publishing articles and things like that. Let's get specific. Let's tell organizations how exactly we can defend against these threats pretty much on a dime.
Mike Krass: Got it. Well, Logan, thank you so much for joining us today.
Outro
To our listeners, that is a wrap for this episode of What's the Problem. I hope you found our conversation with Logan Wolfe to be insightful, to be informative. Remember to tune in next time for more discussions in the world of cyber and data security. I also want to give a quick shout out to our host MKG Marketing. MKG is focused on helping cybersecurity companies get found, get leads, and close deals. So if your cybersecurity business is struggling to generate leads and close deals, let us help you. To learn more, you can visit our website at mkgmarketinginc.com. Thank you for listening. Don't forget to subscribe and leave a rating for the podcast. We appreciate your support. Until next time, my friends.
Logan Wolfe
Logan Wolfe, the founder and CEO of Orana, North America's fastest growing cybersecurity startup, has been involved in the field for 15 years. During his career, he has spearheaded global cybersecurity initiatives at companies like McKesson and led Lloyd's global threat intelligence practice across eight countries, in addition to overseeing critical Telco initiatives in Canada. Orana, under Logan's leadership, provides automated cyber incident detection and response, including regulatory compliance, for all aspects of business operations.


