What's the Problem?with Mike Krass
Hang out with Mike Krass as he learns from cyber security experts on what problem they're facing right now.

Join our weekly newsletter
Get industry news, articles, and tips-and-tricks straight from our experts.
We care about the protection of your data. Read our Privacy Policy.

What’s The Problem
Empower Women in Cybersecurity: Include Women at Every Level of Organization
Jane Frankland talks about the "leaky boat" issue, addressing how women leave tech jobs at unparalleled rates before the age of 35. Listen to Jane as she talks about her key points to attract, develop, and retain women in the world of cybersecurity industry. Also, discover how the cybersecurity field can be described as a "cruel" environment to work in by way of the Attack/Protect mindset we share. (25 minutes)

What’s The Problem
3 Core Tenants of Zero Trust with Neal Dennis of Cyware Labs
Neal Dennis, Cyber Threat Intelligence Consultant at CyWare & Co-Host of the "Adopting Zero Trust" Podcast, joins to discuss the 3 core tenants of zero trust. (23 minutes)
What’s The Problem
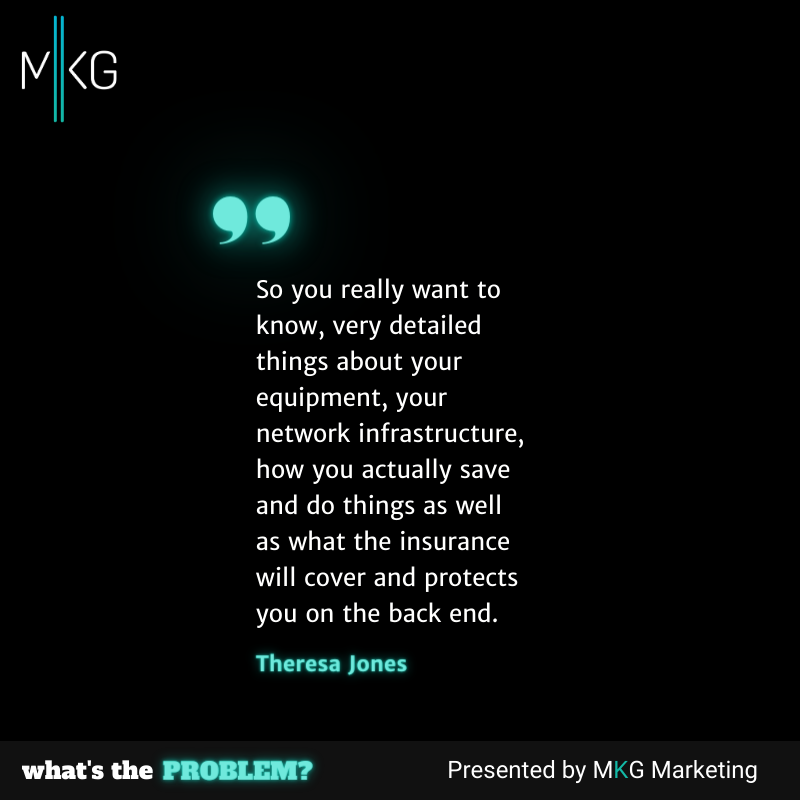
Cybersecurity Insurance "Got Ya's" for Small Business Owners
Join us for an enlightening conversation with Theresa Jones, CEO and owner of Evolve IQ as we explore the realm of small businesses and discuss vital advice on selecting the right cyber insurance policy. Discover essential tips for assessing risks, determining coverage, and establishing incident response plans, all geared toward ensuring your business is well-prepared in the digital age. (18 minutes)

What's the Problem
Ian L. Paterson -Cybersecurity & AI with Plurilock founder Ian L. Paterson
Join us in an enlightening discussion with Ian L. Paterson, CEO of Plurilock, as we discover AI's impact on cybersecurity as it forges strategic illusions. This dynamic interplay blurs the boundary between illusion and innovation when it comes to cybersecurity and Artificial Intelligence.The integration of AI into platforms amplifies recognized security concerns in the evolving landscape. (19 minutes)

What's the Problem
Proactive Defense for Critical Infrastructure | What's the Problem
Join us for an enlightening discussion with Yiyi Miao, Chief Product Officer of OPSWAT, as we explore proactive strategies to strengthen your defense against potential critical infrastructure incidents. (20 minutes)

What's the Problem
Cyber Risk Economics
Jen Moll, Vice President of Strategy & Alliances at Axio, stops by to discuss the economic Impact of Cyber Risks. (20 minutes)

What's the Problem
The Impending CMMC Compliance Deadline with Department of Defense (DoD)
Chase Richardson stops by to discuss the different levels of compliance required for contractors working with the Department of Defense (DoD). (20 minutes)
What's the Problem
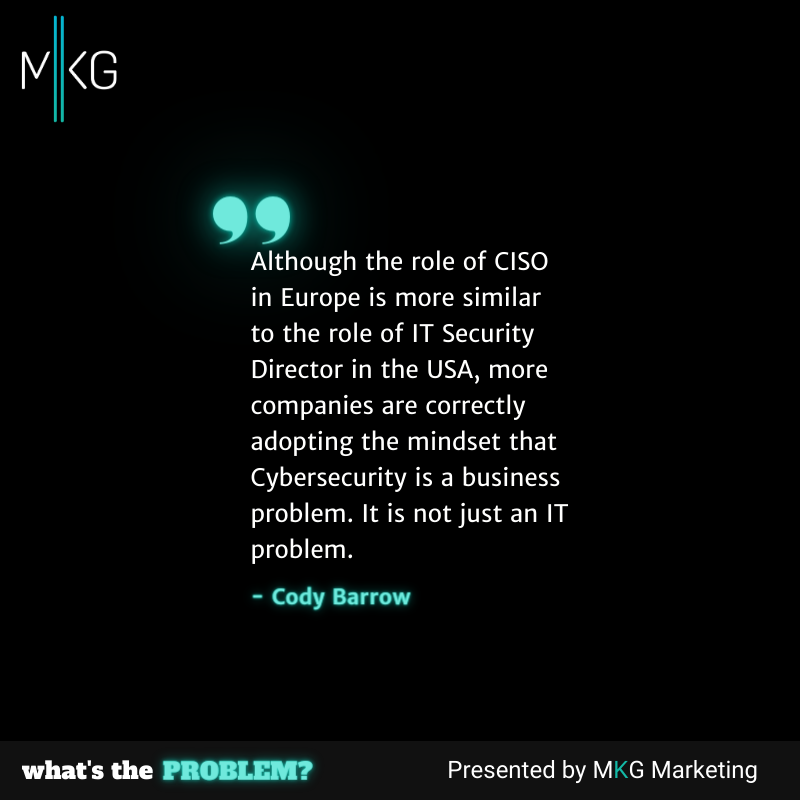
Cybersecurity in the European Union Compared to the United States
Cody Barrow, Chief Strategy Officer at EclecticIQ, stops by to compare and contrast the climate of cyber and data security in Europe versus the United States. (20 minutes)

What's the Problem
How a Challenger Cybersecurity Company Can Navigate Their Product Into a Customers Hands
Andres Andreu, a 30-year veteran of the cybersecurity industry, joins us to discuss what CISOs truly care about during the purchasing cycle. (17 minutes)

What's the Problem
Today's Software Supply Chain through the eyes of the AppSecDev
Derek Weeks, a 30-year veteran of the cybersecurity industry, joins us to discuss open source networks, the importance of a software bill of materials, and much more! (20 minutes)

What's the Problem
How Cybersecurity Integration Partners Work Together
Nick Hansen joins us to discuss cybersecurity integration and how to minimize your attack surface (15 minutes)
What's the Problem
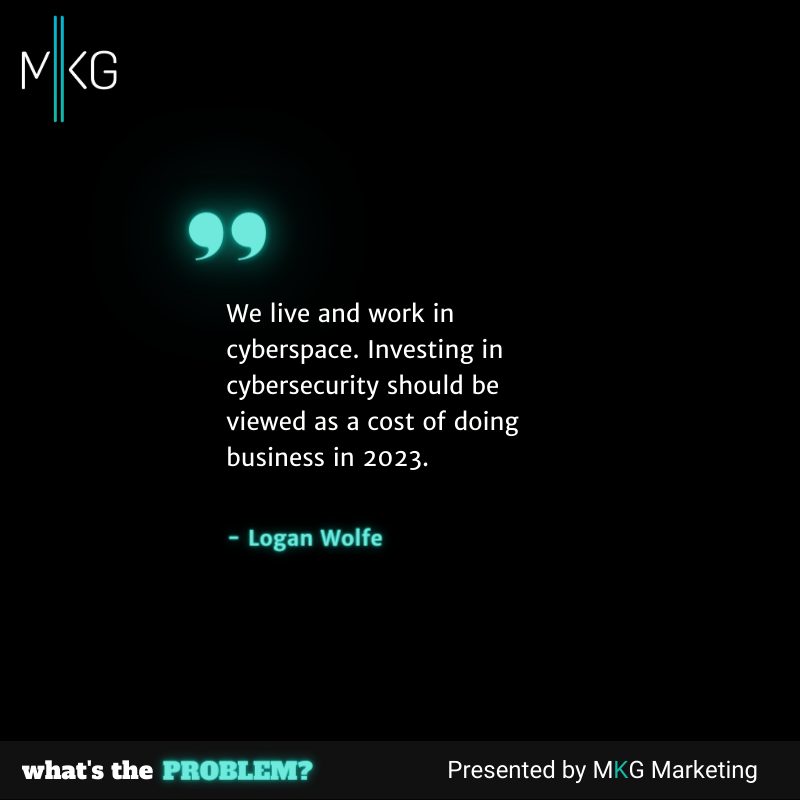
When Policy and Enforcement Converge
Logan Wolfe of ORNA.app joins us to discuss policy and enforcement in the global cybersecurity space. (20 minutes)

What's the Problem
How to Work with Product Marketing at a Cybersecurity Company
Salah Nassar from ZScaler joins us to discuss product marketing and the importance of connecting with your customer. (23 minutes)

What's the Problem
Overlay Architecture: What is It and Who Cares How It Works?
Lauren Malhoit from Men & Mice joins us to discuss Overlay Architecture (24 minutes)

What's the Problem
Data Responsibility in the World of Cybersecurity
Seth Garske from F5 Networks joins us to discuss personalization and the responsible usage of customer data. (21 minutes)

What's the Problem
Effective CISOs: Technical vs Operational
Grant Elliott from Ostendio joins us to discuss how an effective CISO is an operational CISO. Your organization can have all the correct technical systems in place, but if you are missing proper administration, you'll always have vulnerabilities. (18 minutes)
What's the Problem
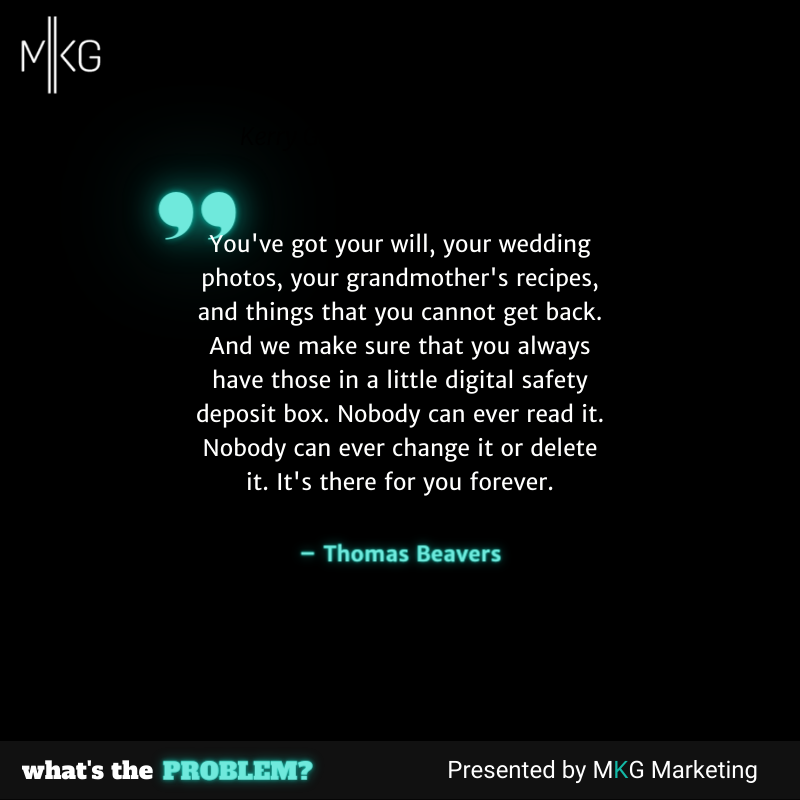
The Future of Cloud Storage Is Blockchain
Join Thomas Beavers of Sollensys as he explains that the future of cloud storage lives on the blockchain - not Dropbox or Google Drive. (12 minutes)

What's the Problem
Programs and Curriculum for Students to Participate in Real-World Cyber Training
Cybersecurity Specialist Selby LeBert of Textron Aviation joins us to discuss programs and curriculum for students to participate in real-world cybersecurity training. (12 minutes)

What's the Problem
What If Cyberweapons Are Not Stored Securely?
What do we need to do to secure and protect cyberweapons? What should we do as a planet if cyberweapons get out? (16 minutes)
What's the Problem
The Ethical Cybersecurity Marketer
Clark Barron, a Senior Demand Generation Strategist with Shippo, joins the podcast to discuss a unicorn topic: the ethical cybersecurity marketer. (22 minutes)
What's the Problem
Procurement Being Involved in The Security Purchase Process
"Reminder: if you've already made the purchase, it's too late to incorporate a thorough OT security look." (21 minutes)

What's the Problem
The Importance of Training on A High Functioning Security Operations Center (SOC)
Jaqueline Lundie joins us to share the importance of training working as a SOC Analyst with the US Department of Health and Human Services. (16 minutes)
What's the Problem
Questions to Ask Security Vendors to Purchase What you Need (and no more!), featuring Alex Titze of Blue Team Alpha
Today, we are speaking with Alex Titze of Blue Team Alpha about the education gap when evaluating security products or solutions. (16 minutes)
What's the Problem
Entry Level Security Roles for Companies such as Textron Aviation with Selby LeBert
Cybersecurity specialist Selby LeBert of Textron Aviation joins us to discuss the rise of entry-level security personnel in the world of security operations for companies such as Textron. (19 minutes)
What's the Problem
A SOC Analysts Point of View on CISA’s Shields Up Directive
A Senior SOC Analyst takes us to the heart of the conversation around CISA shields. Will companies report breaches? Will it help the community as a whole? Listen to Elez Tupuzovic's opinion in this episode. (18 minutes)
What's the Problem
The Journey from Line Cook to the Security Operations Center
In today’s episode, Derek Ireifej of CyberConvoy takes us on his journey from line cook to IT manager to SOC analyst. (27 minutes)

What's the Problem
Security Operation Center (SOC) Analysts = Puzzle Makers
Menekse Saglam presents listeners with the opportunity to step into a Security Operations Center environment from the comfort of your own home. (12 minutes)
What's the Problem
The Year(s) Long Process of Building a Security Program for your Business with Warner Moore of Gamma Force
Listen as Gamma Force CEO Warner Moore describes the common formula he uses to create cybersecurity practices within a business. “An asset that has a vulnerability and a threat has ABC amount of risk to manage.” Curious for more? Tune in to show now. (19 minutes)

What's the Problem
Operational Technology (OT): Which Industries & Regions Lead with Oscar Ruiz
Tune in as Accenture’s Oscar Ruiz tells listeners which global regions and industries are the leaders versus the laggards in the world of Operational Technology (OT). (25 minutes)
What's the Problem
3 States Of Data: In use, In Motion, At Rest
Exploring the concept of confidential computing - securing data in use that is vulnerable/in an unencrypted state - with Fortanix CEO Ambuj Kumar. (15 minutes)

What's the Problem
Endpoint Security's Biggest Issue: Claiming Compliance "Out Of The Box"
Explore the “out of the box” compliance issue in the area of Endpoint Security for both the education and healthcare industries. (11 minutes)

What's the Problem
How Long Does it Take to Train a Cybersecurity Salesperson?
How do you take someone brand new to the world of cybersecurity and turn them into a knowledgeable seller with practical, hands on experience? Join Graham Smith of IBM to hear about their Summit Training program. (25 minutes)
What's the Problem
Incident Response Plans (IRPs). The good, the bad, the ugly.
Learn about IRP's from network security manager James William. (15 minutes)
What's the Problem
To Demand a Ransomware Payment Or Siphon Off Your Intellectual Property?
Chandra Pandey of Seceon joins Mike Krass to discuss ransomware with respect to Intellectual Property (IP), using real-life examples from the Nvidia hack as well as the Microsoft source code hack. (22 minutes)
What's the Problem
Deploy and De-provision Identity Management Controls for a five thousand Employee Hospital Group
Hear the Experience of Nimbus-T CEO Tom Johnson Describes Deploying and De-Provisioning Identity and Access Management Controls for a Large Hospital System. (21 minutes)
What's the Problem
Where Are All the People to Staff Your Security Operations Center (SOC)?
There are more open roles in the security operations center than qualified people to fill them in the United States. What are we going to do about that? (20 minutes)

What's the Problem
When Will Quantum Computing Break 256-bit Encryption?
When Will Quantum Computing Break 256-bit Encryption? Join Bob Zinga, vCISO and Head of Information Security at Directly to find out. (21 minutes)

What's the Problem
Ransomware Threat Vectors: The Danger of Open Ports
Join Information Security Specialist Ravina Joshi to Learn About the Dangers of not cleaning up Open Ports. Think it’s not a big deal? The WannaCry incident begs to differ. (10 minutes)
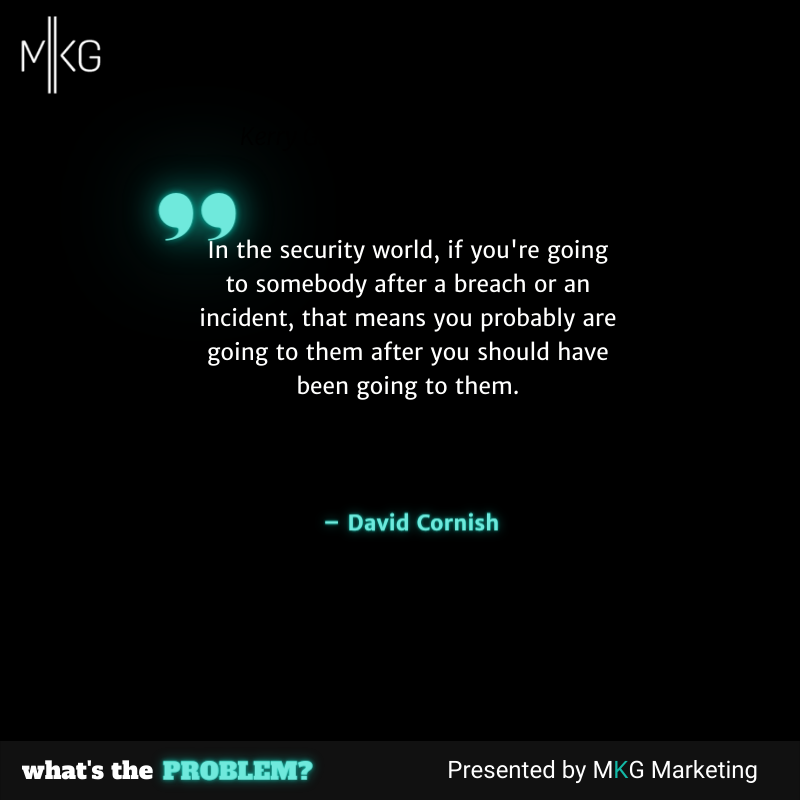
What's the Problem
Identity Breaches: It's Your Partners, Customers or Vendors Leaking Your Information
More often than not, an identity breach is the result of a partner, customer, or vendor breach. Your identity information becomes a casualty of someone else's breach. (14 minutes)
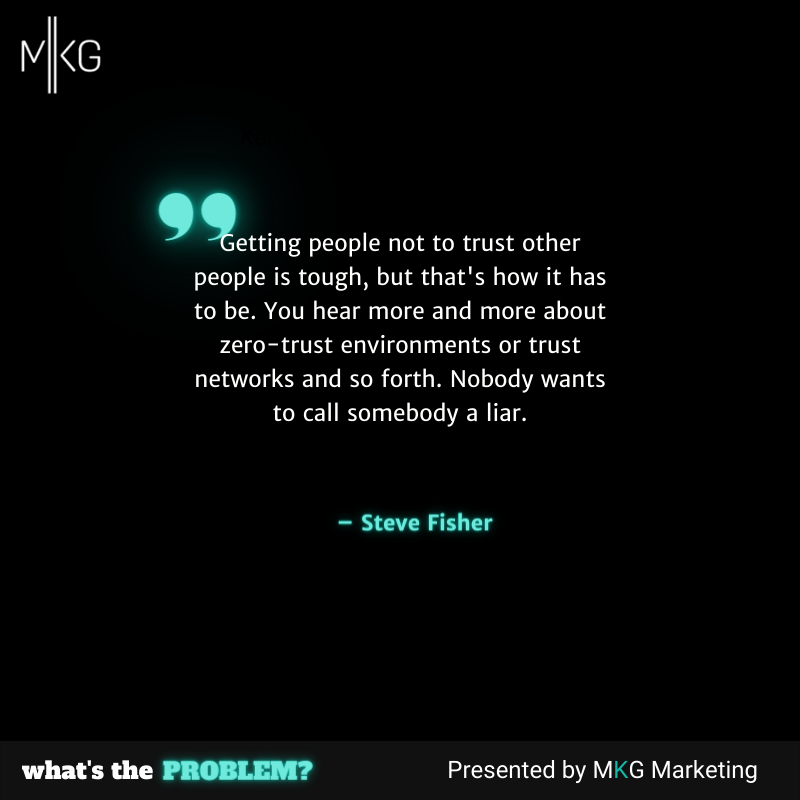
What's the Problem
Cybersecurity in the Education System
Steve Fisher of IMS goes into great detail around the cybersecurity concerns that school systems have to face. He explains how high turnover environments produce opportunities for bad actors as well as dives into the solution: training that people actually a) take, and b) remember! (20 minutes)
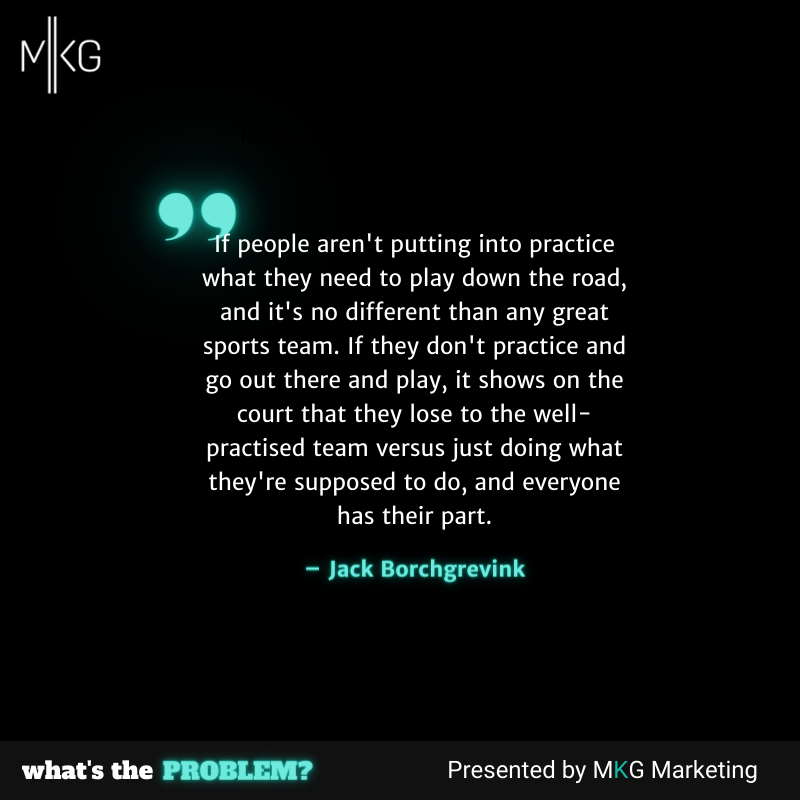
What's the Problem
How to Secure Your Organization During Employee Turnover
Jack Borchgrevink of VMware discusses vendor’s responsibility to provide support in advance of a breach as well as how to secure your organization during times of employee turnover. (16 minutes)
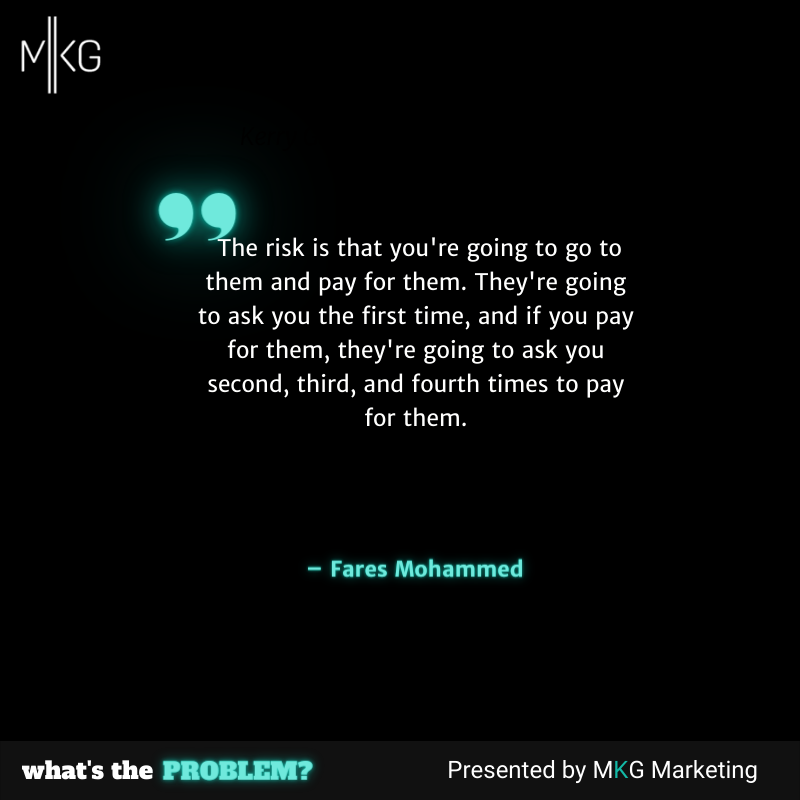
What's the Problem
Case Study: An 85% Compromise Rate through Social Engineering
In this episode, Fares Mohammed joins What’s the Problem to discuss social engineering in the world of #cybersecurity. Email phishing scams about bitcoin or NFT projects all the way down to dropping flash drives in corporate offices to see who would plug them into company networked devices. (17 minutes)
What's the Problem
Creating A New Cybersecurity Category: Phishing Detection & Response (PDR)
Mike Krass chats with Christopher Gibbons to discuss the fact that in 2022 secure email gateways (SEG’s) don’t statistically provide any more protection than you already receive with Microsoft Office 365 or Google Business applications. (18 minutes)
What's the Problem
Speaking to “Technical” versus "Manager" Cybersecurity Buyers
This episode explores a key topic for security vendors to consider: how do I speak to a person in a Technical role versus a Business Manager role? (13 minutes)
What's the Problem
Unwrap the Layers of Password Cracking Attacks
Join security specialist Adil Ahmed as he discusses password cracking attacks such as brute force, password spraying as well as spear phishing when a hacker has gained access to 1 (or more) of your systems to use as hop points. (15 minutes)

What's the Problem
How to Avoid Pressure to Achieve Short Term Results at the Sacrifice of Long Term Strategy in Cyber Security
In this episode, Dani Woolf dives into the big H word: Honesty. More specifically, Dani spends time discussing how honesty and transparency around what your security product can or cannot do for the buyers organization is a critical currency to trade in and should not be taken lightly. (17 minutes)

What's the Problem
Open Source Cyber Security to Support Finding Missing Persons
In this episode, Mike Krass chats with Matthew Buhler about his security analysis work to assist in the recovery of missing persons as well as the removal of CSAM (Child Sexual Abuse Material) from the Internet. (11 minutes)

What's the Problem
Cyber Security for SMBs
In this episode, Mike Krass explores how Small-to-Midsize businesses are often targets of Cyber attacks with Marcela Denniston. Marcela is a security engineer, entrepreneur, and marketing leader with a background in the public and private sectors. (20 minutes)

What's the Problem?
Phishing
In this episode, Ebony Hall, a Systems Engineer with Cambium Learning who also has an IT background in the military (U.S. Army), discusses phishing attacks in the public sector as well as for commercial organizations. (10 minutes)
What's the Problem?
The Convergence of Cloud and Data
In this episode, Mike Krass chats with Andy Smith the Chief Marketing Officer at Laminar to discuss the problems of security buyers: the convergence of cloud transformation and data democratization. (10 minutes)